1. What is a ConfigMap in Kubernetes?
A ConfigMap in Kubernetes is an API object used to
store non-sensitive configuration data as key-value pairs.
i)
Storage: key-value pairs stored in Kubernetes’ etcd
datastore.
ii)
Management: Handled by the Kubernetes
API server.
iii)
Access: Managed via kubectl CLI or
Kubernetes API.
iv) ConfigMaps in Kubernetes separate configuration from application code, making applications more portable, reusable, and flexible.
v)
The
length of the key should not be more than 1MB.
i)
NameSpace
A pods cannot use confiMaps of Namespace B.
ii)
Pods will
use the config map of the namespace in which they are created and cannot use
any other namespace config map.
2. ConfigMaps can be created in two ways.
i) Imperative
way:- Create by command line.
ii) Declarative
way:- Create by yaml file.
1). Imperative.
:-
Literal:
i) Single
key pairs.
# kubectl
create configmap <Name> --from-literal=<key>=<value>
ii) Multiple
key pairs
# kubectl
create configmap <Name> --from-literal=<key1>=<value1> --from-literal=<key2>=<value2>
iii) From File/Directory: Load
configuration from files or folders.
# kubectl
create configmap <Name> --from-file=<FileName>
# kubectl
create configmap <Name> --from-file=<DirectoryName/>
2). Declarative:-
i) Inline YAML: Define
directly in YAML manifests.
3. How to Check If ConfigMap Data Exceeds 1MB.
# kubectl
get configmap configmap-name -o json | jq '.data | map_values(length)'
{
"name_key": 12
}
12 bytes
4. How to create ConfigMap.
Imperative
and declarative.
1). Imperative:-
Literal:
a) Create a Single
key pairs
# kubectl create configmap <Name>
--from-literal=<key>=<value>
# kubectl
get cm
# kubectl
describe cm configmap-test
b) ConfigMap use in the yaml file.
# vim configmap-1.yaml
apiVersion:
v1
kind: Pod
metadata:
name: configmap-demo-1
spec:
containers:
- name: demo-container
image: nginx
envFrom:
- configMapRef:
name: configmap-test
# kubectl exec -it configmap-demo-1 -- printenv
a) How to create the Multiple key pairs ?
# kubectl
create configmap <Name> --from-literal=<key1>=<value1> --from-literal=<key2>=<value2>
# kubectl
create configmap configmap-test --from-literal=conf_Name=first-test
--from-literal=conf_Name2=second-test
# kubectl
describe cm configmap-test
b) How to use a single key in the yaml file.
# vim configmap-2.yaml
apiVersion:
v1
kind: Pod
metadata:
name: configmap-demo-2
spec:
containers:
- name: demo-container
image: nginx
env:
- name: testing
valueFrom:
configMapKeyRef:
name: configmap-test
key: conf_Name2
# kubectl exec -it configmap-demo-2 -- printenv
a) From
File/Directory: Load configuration from files or folders.
# kubectl
create configmap <Name> --from-file=<FileName>
# kubectl
create configmap <Name> --from-file=<DirectoryName/>
# vim
data-file
username="shashikant"
password="123456
# kubectl
create configmap configmap-3 --from-file=data-file
b) How to mount the data-file.txt file in the yaml file.
# vim
configmap-3.yaml
apiVersion:
v1
kind: Pod
metadata:
name: configmap-demo-3
spec:
containers:
- name: demo-container
image: nginx
volumeMounts:
- name: config
mountPath: /etc/config
volumes:
- name: config
configMap:
name: configmap-3
# kubectl
apply -f configmap-3.yaml
# kubectl
exec -it configmap-demo-3 -- bash
2. Declarative:-
a) Inline
YAML: Define directly in YAML manifests.
# vim configmap.yaml
apiVersion:
v1
kind: ConfigMap
metadata:
name: inline-config
data:
app_name: myapp
app_version: "1.0"
database_url:
jdbc:mysql://localhost:3306/mydb
How to edit configMaps.
Imperative:-
# kubectl
edit configmap <configmap-Name>
or
Declarative:-
a) Create a yaml file then edit and apply.
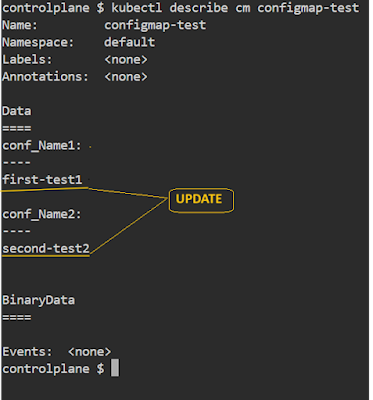
# kubectl get configmap configmap-test -o yaml > configmap.yaml
# vim
configmap.yaml
apiVersion:
v1
kind:
ConfigMap
metadata:
name: configmap-test
namespace: default
data:
conf_Name1: first-test1
conf_Name2: second-test2
# kubectl
apply -f configmap.yaml
How to
Delete configMaps.
# kubectl
delete cm <configmap-Name>
# kubectl
delete -f configmap.yaml
ConfigMap vs Secrets:-
|
Feature |
ConfigMap |
Secrets |
|
Purpose |
Stores
non-sensitive configuration data |
Stores
sensitive or confidential information |
|
Data
Encryption |
Data is
not encrypted |
Data is
encrypted |
|
Use
Cases |
Storing
environment variables, configuration files, etc. |
Storing
sensitive data like passwords, API keys, certificates |
|
Access
Control |
Accessible
to all pods within the cluster |
Restricted
access based on RBAC policies |
|
Kubernetes API |
Kubernetes
API object of type |
Kubernetes
API object of type |
|
Visibility |
Configurations
are visible in plain text |
Encrypted
data is not visible in plain text |
|
Usage |
Suitable
for non-sensitive data that needs to be shared |
Suitable
for sensitive data that requires encryption |











No comments:
Post a Comment